Can You Upload Abusive Stories on Tapas
Corruption Case Cheat Canvas¶
Introduction¶
Often when the security level of an application is mentioned in requirements, the post-obit expressions are met:
- The application must be secure.
- The awarding must defend against all attacks targeting this category of application.
- The application must defend against attacks from the OWASP Top ten
- ...
These security requirements are too generic, and thus useless for a development team...
In gild to build a secure application, from a pragmatic point of view, it is important to place the attacks which the application must defend confronting, co-ordinate to its business organization and technical context.
Objective¶
The objective of this crook sheet is to provide an explanation of most what an Abuse Case is, why corruption cases are important when considering the security of an application, and farther finally, to provide a proposal for a businesslike approach to building a list of abuse cases and tracking them for every feature planned for implementation as role of an application. The cheat sheet may be used for this purpose regardless of the project methodology used (waterfall or agile).
Important annotation near this Crook Sheet:
The main objective is to provide a pragmatic approach in guild to permit a company or a project team to first building and treatment the listing of abuse cases then customize the elements proposed to its context/civilisation in order to, finally, build its own method. This cheat sheet can be seen as a getting-started tutorial. Context & arroyo¶
Why clearly place the attacks¶
Clearly identifying the attacks against which the application must defend is essential in order to enable the following steps in a projection or sprint:
- Evaluate the business organisation take chances for each of the identified attacks in order perform a selection according to the business concern risk and the project/sprint budget.
- Derive security requirements and add together them into the projection specification or sprint's user stories and acceptance criteria.
- Judge the overhead of provision in the initial project/sprint charge that will be necessary to implement the countermeasures.
- Almost countermeasures: Allow the project team to ascertain them, and to determine in which location they are appropriate (network, infrastructure, code...) to be located.
Notion of Abuse Instance¶
In order to help build the list of attacks, the notion of Abuse Cases is helpful.
An Abuse Case can be defined equally:
A style to use a characteristic that was not expected by the implementer, allowing an attacker to influence the feature or outcome of use of the characteristic based on the attacker action (or input). Synopsys define an Abuse Instance like this:
Misuse and abuse cases draw how users misuse or exploit the weaknesses of controls in software features to assail an application. This tin lead to tangible business organization impact when a straight assault against business functionalities, which may bring in revenue or provide positive user experience, are attacked. Abuse cases can also be an effective way to drive security requirements that lead to proper protection of these critical business organization use cases. Synopsys source
How to define the listing of Corruption Cases¶
In that location are many dissimilar ways to ascertain the list of abuse cases for a feature (that can be mapped to a user story in agile projects).
The project OWASP Open SAMM proposes the following approach in the Stream B of the Security Exercise Requirements Driven Testing for the Maturity level 2:
Misuse and abuse cases describe unintended and malicious use scenarios of the application, describing how an aggressor could do this. Create misuse and corruption cases to misuse or exploit the weaknesses of controls in software features to attack an awarding. Utilize abuse-example models for an application to serve equally fuel for identification of physical security tests that direct or indirectly exploit the abuse scenarios. Abuse of functionality, sometimes referred to equally a "business logic assault", depends on the blueprint and implementation of awarding functions and features. An example is using a password reset menses to enumerate accounts. As part of business organization logic testing, identify the business rules that are important for the awarding and turn them into experiments to verify whether the application properly enforces the business rule. For case, on a stock trading awarding, is the attacker allowed to starting time a trade at the starting time of the day and lock in a price, agree the transaction open until the end of the day, and so consummate the sale if the stock price has risen or abolish if the toll dropped? Open SAMM source: Verification Requirement Driven Testing Stream B
Another style to achieve the building of the list can exist the following (more bottom-up and collaboratively oriented):
Brand a workshop that includes people with the following profiles:
- Business analyst: Will be the business key people that will describe each characteristic from a business concern point of view.
- Risk annotator: Volition exist the company's risk personnel that will evaluate the business risk from a proposed set on (sometimes it is the Business analyst depending on the visitor).
- Penetration tester: Will be the attacker that will propose attacks that they can perform on the business characteristic(south) in question. If the company does non have a person with this profile and so information technology is possible to request the service of an external specialist. If possible, include ii penetration testers with different backgrounds in order to increase the number of possible attacks that will be identified and considered.
- Technical leaders of the projects: Will be the projection technical people and will allow technical substitution about attacks and countermeasures identified during the workshop.
- Quality balls annotator or functional tester: Personnel that may accept a good sense of how the awarding/functionality is intended to work (positive testing), not work (negative testing), and what things cause information technology to fail (failure cases).
During this workshop (duration will depend on the size of the feature listing, but iv hours is a expert start) all concern features that will be office of the project or the sprint volition be candy. The output of the workshop will be a list of attacks (abuse cases) for all business features. All abuse cases will have a risk rating that allows for filtering and prioritization.
It is important to take into account Technical and Business kind of abuse cases and marking them accordingly.
Example:
- Technical flagged abuse example: Add Cantankerous Site Scripting injection into a comment input field.
- Business flagged abuse case: Ability to change capricious the price of an article in an online shop prior to pass an club causing the user to pay a lower amount for the wanted article.
When to define the listing of Abuse Cases¶
On agile project, the definition workshop must be made after the meeting in which User Stories are included in a Dart.
In waterfall projects, the definition workshop must exist made when the business feature to implements are identified and known by the business.
Whatever the fashion of project used (agile or waterfall), the abuse cases selected to be addressed must become security requirements in each characteristic specification department (waterfall) or User Story acceptance criteria (agile) in order to allow additional cost/effort evaluation, identification and implementation of the countermeasures.
Each abuse case must have a unique identifier in order to allow tracking throughout the whole project/sprint (details about this signal will be given in the proposal section).
An example of unique ID format can be ABUSE_CASE_001.
The following effigy provides an overview of the chaining of the different steps involved (from left to right):
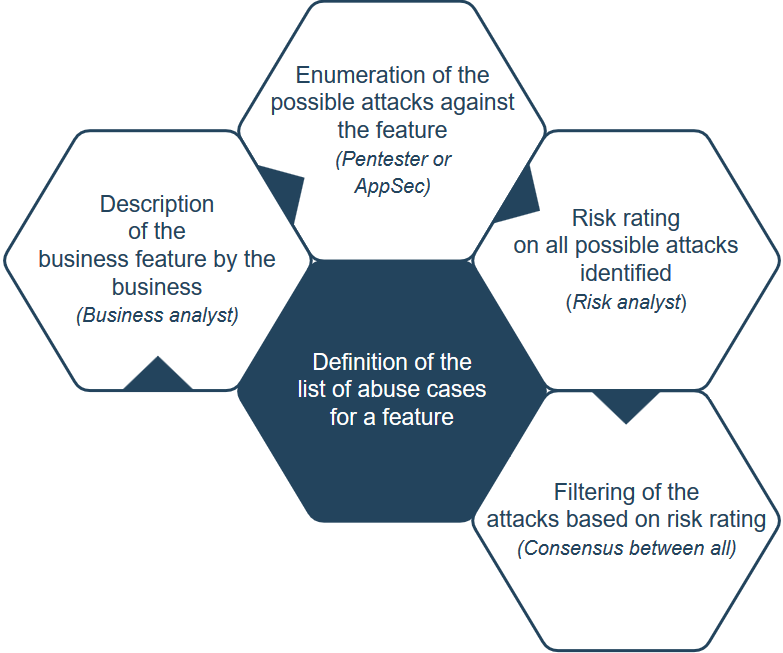
Proposal¶
The proposal will focus on the output of the workshop explained in the previous section.
Step ane: Training of the workshop¶
First, even if it seems obvious, the fundamental concern people must be certain to know, understand and be able to explain the business features that will be processed during the workshop.
Secondly, create a new Microsoft Excel file (you can also use Google Sheets or any other like software) with the following sheets (or tabs):
- FEATURES
- Will contain a table with the list of business features planned for the workshop.
- Corruption CASES
- Will incorporate a tabular array with all corruption cases identified during the workshop.
- COUNTERMEASURES
- Volition comprise a table with the list of possible countermeasures (low-cal description) imagined for the abuse cases identified.
- This canvass is non mandatory, but it tin can be useful (for an abuse instance to know), if a fix is easy to implement and and so can affect the risk rating.
- Countermeasures can be identified by the AppSec profile during the workshop, because an AppSec person must exist able to perform attacks but besides to build or place defenses (it is not e'er the case for the Pentester profile considering this person's focus is more often than not on the attack side only, so, the combination Pentester + AppSec is very efficient to take a 360 caste view).
This is the representation of each sheet forth with an example of content that will be filled during the workshop:
FEATURES sheet:
| Characteristic unique ID | Feature name | Feature brusque description |
|---|---|---|
| FEATURE_001 | DocumentUploadFeature | Allow user to upload document along a message |
COUNTERMEASURES sail:
| Countermeasure unique ID | Countermeasure short description | Countermeasure help/hint |
|---|---|---|
| DEFENSE_001 | Validate the uploaded file by loading information technology into a parser | Use advice from the OWASP Crook Sheet about file upload |
Abuse CASES sheet:
| Corruption case unique ID | Feature ID impacted | Abuse instance's assail description | Set on referential ID (if applicable) | CVSS V3 risk rating (score) | CVSS V3 string | Kind of abuse case | Countermeasure ID applicable | Handling determination (To Address or Risk Accepted) |
|---|---|---|---|---|---|---|---|---|
| ABUSE_CASE_001 | FEATURE_001 | Upload Office file with malicious macro in charge of dropping a malware | CAPEC-17 | HIGH (7.7) | CVSS:3.0/AV:North/Air-conditioning:H/PR:L/UI:R/Southward:C/C:N/I:H/A:H | Technical | DEFENSE_001 | To Address |
Step 2: During the workshop¶
Use the spreadsheet to review all the features.
For each feature, follow this flow:
- Key business concern people explain the electric current feature from a concern point of view.
- Penetration testers suggest and explicate a ready of attacks that they tin perform confronting the feature.
-
For each assault proposed:
- Appsec proposes a countermeasure and a preferred ready location (infrastructure, network, code, design...).
- Technical people give feedback about the feasibility of the proposed countermeasure.
- Penetration testers use the CVSS v3 (or other standard) calculator to determine a risk rating. (ex: CVSS V3 computer)
- Hazard key people accept/increment/decrease the rating to have last i that match the real business concern impact for the company.
-
Business, Take chances and Technical key peoples notice a consensus and filter the list of abuses for the electric current feature to keep the ones that must be addressed, so flag them appropriately in the Corruption CASES canvass (if risk is accepted then add a comment to explicate why).
- Pass to next characteristic...
If the presence of penetration testers is not possible and so you tin use the following references to place the applicable attacks on your features:
- OWASP Automated Threats to Web Applications
- OWASP Testing Guide
- OWASP Mobile Testing Guide
- Common Attack Blueprint Enumeration and Classification (CAPEC)
Important notation on attacks and countermeasure noesis base(s):
With the time and across projects, you lot will obtain your own dictionary of attacks and countermeasures that are applicative to the kind of application in your business domain. This dictionary will speed upwardly the future workshops in a significant way. To promote the cosmos of this dictionary, you can, at the end of the projection/dart, gather the list of attacks and countermeasures identified in a central location (wiki, database, file...) that will be used during the side by side workshop in combination with input from penetration pesters. Footstep iii: After the workshop¶
The spreadsheet contains (at this stage) the list of all abuse cases that must exist handled and, potentially (depending on the chapters) corresponding countermeasures.
At present, there are two remaining task:
- Fundamental business people must update the specification of each feature (waterfall) or the User Story of each feature (agile) to include the associated abuse cases as Security Requirements (waterfall) or Credence Criteria (agile).
- Key technical people must evaluate the overhead in terms of charge/endeavour to have into business relationship the countermeasure.
Step 4: During implementation - Abuse cases treatment tracking¶
In order to track the handling of all the abuse cases, the post-obit approach can exist used:
If one or several abuse cases are handled at:
- Design, Infrastructure or Network level
- Make a annotation in the documentation or schema to indicate that This design/network/infrastructure takes into account the abuse cases ABUSE_CASE_001, ABUSE_CASE_002, ABUSE_CASE_xxx.
- Code level
- Put a special comment in the classes/scripts/modules to indicate that This class/module/script takes into business relationship the abuse cases ABUSE_CASE_001, ABUSE_CASE_002, ABUSE_CASE_xxx.
- Dedicated note like
@AbuseCase(ids={"ABUSE_CASE_001","ABUSE_CASE_002"})tin exist used to facilitate tracking and allow identification into integrated development surround.
Using this way, it becomes possible (via some pocket-sized scripting) to identify where abuse cases are addressed.
Step v: During implementation - Corruption cases handling validation¶
As abuse cases are defined, it is possible to put in place automated or manual validations to ensure that:
- All the selected abuse cases are handled.
- An abuse instance is correctly/completely handled.
Validations can be of the following kinds:
- Automated (run regularly at commit, daily or weekly in the Continuous Integration Jobs of the project):
- Custom audit rules in Static Application Security Testing (SAST) or Dynamic Application Security Testing (DAST) tools.
- Defended unit, integration or functional security oriented tests.
- ...
- Manual:
- Security lawmaking review betwixt projection's peers during the design or implementation.
- Provide the list of all abuse cases addressed to pentesters so that they may validate the protection efficiency for each abuse example during an intrusion exam against the application (the pentester volition validate that the attacks identified are no longer effective and will also try to find other possible attacks).
- ...
Calculation automated tests besides allow teams to track that countermeasures confronting the abuse cases are still effective/in place during a maintenance or bug fixing phase of a project (to prevent accidental removal/disabling). It is as well useful when a Continuous Commitment approach is used, to ensure that all abuse cases protections are in place before opening access to the application.
Example of derivation of Corruption Cases every bit User Stories¶
The following department testify an example of derivation of Abuse Cases equally User Stories, hither using the OWASP Peak 10 every bit input source.
Threat Oriented Personas:
- Malicious User
- Abusive User
- Unknowing User
A1:2017-Injection¶
Ballsy:
Almost any source of data tin can be an injection vector, environment variables, parameters, external and internal web services, and all types of users. Injection flaws occur when an aggressor tin can send hostile data to an interpreter.
Abuse Case:
As an attacker, I will perform an injection attack (SQL, LDAP, XPath, or NoSQL queries, Bone commands, XML parsers, SMTP headers, expression languages, and ORM queries) against input fields of the User or API interfaces
A2:2017-Cleaved Authentication¶
Ballsy:
Attackers have access to hundreds of millions of valid username and password combinations for credential stuffing, default administrative account lists, automated brute force, and dictionary assail tools. Session direction attacks are well understood, particularly in relation to unexpired session tokens.
Abuse Case:
As an assaulter, I have access to hundreds of millions of valid username and password combinations for credential stuffing.
Abuse Case:
As an assaulter, I have default administrative account lists, automated brute strength, and dictionary assault tools I apply confronting login areas of the application and support systems.
Abuse Case:
As an assailant, I manipulate session tokens using expired and fake tokens to gain access.
A3:2017-Sensitive Data Exposure¶
Epic:
Rather than directly attacking crypto, attackers steal keys, execute man-in-the-middle attacks, or steal clear text information off the server, while in transit, or from the user's customer, e.thousand. browser. A manual attack is by and large required. Previously retrieved password databases could exist creature forced by Graphics Processing Units (GPUs).
Corruption Case:
As an assaulter, I steal keys that were exposed in the application to get unauthorized admission to the awarding or system.
Abuse Case:
Every bit an assaulter, I execute man-in-the-heart attacks to become access to traffic and leverage it to obtain sensitive information and possibly go unauthorized access to the application.
Abuse Case:
As an aggressor, I steal articulate text information off the server, while in transit, or from the user's client, e.g. browser to go unauthorized access to the application or system.
Abuse Case:
Every bit an assailant, I find and target one-time or weak cryptographic algorithms by capturing traffic and breaking the encryption.
A4:2017-XML External Entities (XXE)¶
Ballsy:
Attackers tin exploit vulnerable XML processors if they can upload XML or include hostile content in an XML document, exploiting vulnerable code, dependencies or integrations.
Corruption Case:
As an attacker, I exploit vulnerable areas of the awarding where the user or system tin can upload XML to extract data, execute a remote asking from the server, scan internal systems, perform a deprival-of-service attack, likewise every bit execute other attacks.
Abuse Case:
As an assailant, I include hostile content in an XML document which is uploaded to the application or system to excerpt data, execute a remote request from the server, scan internal systems, perform a denial-of-service set on, besides as execute other attacks.
Abuse Case:
As an assailant, I include malicious XML lawmaking to exploit vulnerable lawmaking, dependencies or integrations to extract information, execute a remote request from the server, scan internal systems, perform a denial-of-service assault (e.thou. Billion Laughs assault), as well as execute other attacks.
A5:2017-Broken Access Control¶
Epic:
Exploitation of access control is a core skill of attackers. Admission control is detectable using manual means, or possibly through automation for the absenteeism of access controls in certain frameworks.
Corruption Case:
As an attacker, I bypass admission control checks by modifying the URL, internal application land, or the HTML page, or simply using a custom API attack tool.
Corruption Case:
As an attacker, I dispense the chief key and modify it to access another's users record, assuasive viewing or editing someone else'south account.
Abuse Case:
As an assaulter, I manipulate sessions, access tokens, or other admission controls in the application to act as a user without being logged in, or acting as an admin/privileged user when logged in as a user.
Corruption Instance:
As an attacker, I leverage metadata manipulation, such as replaying or tampering with a JSON Web Token (JWT) access control token or a cookie or hidden field manipulated to elevate privileges or abusing JWT invalidation.
Abuse Case:
As an attacker, I exploit Cross-Origin Resource Sharing CORS misconfiguration assuasive unauthorized API access.
Corruption Case:
As an attacker, I force browsing to authenticated pages as an unauthenticated user or to privileged pages every bit a standard user.
Corruption Case:
Every bit an assailant, I access APIs with missing access controls for POST, PUT and DELETE.
Corruption Example:
Every bit an attacker, I target default crypto keys in employ, weak crypto keys generated or re-used, or keys where rotation missing is missing.
Abuse Case:
As an aggressor, I find areas where the user agent (e.g. app, post client) does not verify if the received server document is valid and perform attacks where I get unauthorized access to data.
A6:2017-Security Misconfiguration¶
Epic:
Attackers will often endeavour to exploit unpatched flaws or admission default accounts, unused pages, unprotected files and directories, etc to proceeds unauthorized access or noesis of the system.
Abuse Case:
As an aggressor, I find and exploit missing appropriate security hardening configurations on any part of the awarding stack, or improperly configured permissions on deject services.
Abuse Example:
As an attacker, I find unnecessary features which are enabled or installed (e.g. unnecessary ports, services, pages, accounts, or privileges) and assault or exploit the weakness.
Abuse Case:
As an attacker, I employ default accounts and their passwords to admission systems, interfaces, or perform actions on components which I should not exist able to.
Abuse Instance:
As an attacker, I find areas of the application where error handling reveals stack traces or other overly informative fault messages I can use for further exploitation.
Abuse Case:
As an attacker, I find areas where upgraded systems, latest security features are disabled or non configured securely.
Abuse Case:
As an aggressor, I find security settings in the application servers, application frameworks (e.1000. Struts, Spring, ASP.Cyberspace), libraries, databases, etc. not set to secure values.
Abuse Case:
Equally an attacker, I find the server does not send security headers or directives or they are non set to secure values.
A7:2017-Cross-Site Scripting (XSS)¶
Epic:
XSS is the second most prevalent issue in the OWASP Top x, and is found in around two-thirds of all applications.
Abuse Example:
Every bit an aggressor, I perform reflected XSS where the awarding or API includes unvalidated and unescaped user input as part of HTML output. My successful set on tin allow the attacker to execution of arbitrary HTML and JavaScript in my victim's browser. Typically the victim volition demand to interact with some malicious link that points to an assailant-controlled page, such equally malicious watering pigsty websites, advertisements, or like.
Abuse Example:
As an assaulter, I perform stored XSS where the awarding or API stores unsanitized user input that is viewed at a afterward time by some other user or an administrator.
Abuse Case:
Equally an attacker, I perform DOM XSS where JavaScript frameworks, unmarried-page applications, and APIs that dynamically include attacker-controllable data to a page is vulnerable to DOM XSS.
A8:2017-Insecure Deserialization¶
Epic:
Exploitation of deserialization is somewhat hard, as off-the-shelf exploits rarely work without changes or tweaks to the underlying exploit code.
Abuse Instance:
As an assaulter, I find areas of the application and APIs where deserialization of hostile or tampered objects can exist supplied. As a event, I can focus on an object and data structure related attacks where the attacker modifies application logic or achieves capricious remote code execution if there are classes available to the application that can change beliefs during or later on deserialization. Or I focus on data tampering attacks such as access-control-related attacks where existing data structures are used but the content is changed.
A9:2017-Using Components with Known Vulnerabilities¶
Ballsy:
While information technology is like shooting fish in a barrel to find already-written exploits for many known vulnerabilities, other vulnerabilities crave concentrated effort to develop a custom exploit.
Corruption Case:
Every bit an assailant, I detect common open up source or closed source packages with weaknesses and perform attacks against vulnerabilities and exploits which are disclosed
A10:2017-Insufficient Logging & Monitoring¶
Epic:
Exploitation of insufficient logging and monitoring is the boulder of nearly every major incident. Attackers rely on the lack of monitoring and timely response to achieve their goals without existence detected. In 2016, identifying a alienation took an average of 191 days and so enough of time for harm to be inflicted.
Abuse Case:
Equally an assailant, I assail an system and the logs, monitoring systems, and teams exercise non see or respond to my attacks.
Sources of the schemas¶
All figures were created using https://www.draw.io/ site and exported (as PNG paradigm) for integration into this article.
All XML descriptor files for each schema are available below (using XML description, modification of the schema is possible using Describe.IO site):
Schemas descriptors archive
Source: https://cheatsheetseries.owasp.org/cheatsheets/Abuse_Case_Cheat_Sheet.html
0 Response to "Can You Upload Abusive Stories on Tapas"
Post a Comment